The University of Waterloo's Information Risk and Privacy Impact Assessment (IRA-PIA) program
The intentions of this program include:
-
Identify and understand potential privacy and IT security risks associated with new or redesigned university business processes or services that handle Restricted and Highly Restricted information under Policy 46 – Information Management, including Personal Information as defined by Ontario's Freedom of Information and Protection of Privacy Act, RSO 1990, c F.31 (FIPPA).
-
Prevent or mitigate adverse privacy and IT security outcomes.
-
Enhance privacy and IT security protections.
-
Assist Information Stewards in making informed decisions about proceeding with initiatives.
-
Ensure compliance with FIPPA, as amended by Bill 194, which mandates Privacy Impact Assessments (PIAs) for certain projects.
When to Engage in an IRA-PIA
Under the amendments introduced by Bill 194, effective July 1, 2025, under sections 38(3) and (5) of FIPPA, before collecting personal information, or making any significant change to the collection, use, or disclosure of personal information, public sector institutions, including universities, are required to conduct IRA-PIAs.
To determine whether your project requires an IRA-PIA, please consider the following questions:
-
Is this a new program or project that will involve collection, use, or disclosure of Restricted or Highly Restricted information, under Policy 46, including Personal Information, as defined by FIPPA?
-
Does it involve major changes to existing programs that significantly alter the handling of such information?
-
Will it utilize new technologies known to impact privacy (e.g., biometrics, surveillance tools)?
-
Does it entail substantial modifications to technology affecting information management, access, or IT security features?
-
Will it create or modify databases containing sensitive information, especially those linking multiple data sources?
-
Does it involve new or modified identification and authentication systems, such as multi-purpose identifiers or biometric systems?
-
Are there other significant changes to the handling of Restricted or Highly Restricted information not covered above?
-
Is equipment involved that will be connected to the University of Waterloo network?
If you answer "Yes" to any of these questions - please complete and submit the IRA-PIA intake form. This process will initiate the necessary assessments to ensure your initiative complies with privacy and IT security requirements.
If all answers to these questions are "No" - your project may proceed without an IRA-PIA. However, should the scope or nature of the project change, re-evaluation is necessary to determine if an IRA-PIA is required.
When a Privacy Impact Assessment (PIA) may be required on its own
Privacy Impact Assessment (PIA) may be required on its own—without an Information Risk Assessment (IRA)—when the main concern is privacy, especially legal compliance under FIPPA or the Personal Health Information Protection Act, 2004, S.O. 2004, c.3 (PHIPA), but not information security or broader information risk. Please review the questions below to determine whether it is necessary to complete a PIA only.
-
Is there no significant use or change to technology or security infrastructure, but the collection, use, or disclosure of personal information is changing? (e.g., your project includes a new form or process that collects more personal information, or different information, than before.)
-
Does the project involve personal information but not sensitive IT systems or high-risk data types? (e.g., your project will share contact information with third parties.)
-
Is the objective only to fulfill the PIA requirement under Bill 194 and sections 38(3) and (5) of FIPPA?
-
Does the project rely on entirely non-digital means and low-technology? (e.g., the intake form is paper-based, and materials may be scanned and shared by email.)
-
Does the project only involve personal information that is minimally sensitive, and there is no major IT security, operational, or legal risk to assess beyond privacy concerns?
If you are still uncertain whether a PIA is required, please use the PIA decision tree to help guide your decision.
If you assess a PIA alone is necessary, please complete and retain a copy of the PIA form. This process ensures your project, or use of disclosure of personal information, complies with privacy requirements under FIPPA. You must retain the completed PIA so that it is available for review if requested by the Information and Privacy Commissioner of Ontario.
Understanding the PIA process
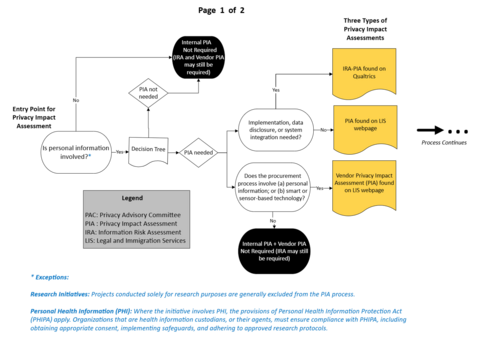
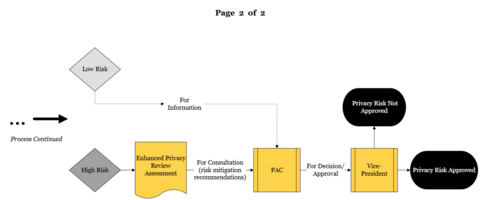
IRA-PIA Process Continued
What happens after you submit the IRA-PIA intake form?
Intake forms are reviewed by the Privacy Team with Legal and Immigration Services, and the Information Security Services group, within Information Systems and Technology, are made thereon, and ownership of the findings resides with the relevant Information Steward(s).
Timeline
It typically takes 2–4 weeks (depending on initiative complexity) to review and respond to IRA-PIAs or PIAs.
Still have questions?
If you are unsure whether an IRA-PIA, PIA, or IRA is necessary, please contact PIA@uwaterloo.ca.