Abstract
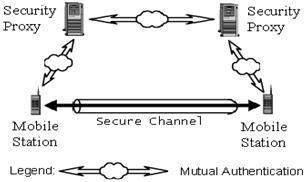
Current authentication technologies are commonly based asymmetric encryption techniques such as digital signatures. To be able to employ these techniques requires a significant amount of computing resources, which are uncommon to many lightweight mobile devices such as cell phones and personal digital assistants (PDAs). It is therefore currently infeasible or uneconomical to implement mutual authentication services between these devices. A new protocol called “Controlled Proxy-Assisted Secure End-to-End Communication Protocol” was proposed by Professor Hung-Yu Lin to solve the problem. The goal of a Fourth Year Design Project at the University of Waterloo of Jimmy Choi, Kenneth Choi, Kenric Li, and Truman Ng supervised by Prof. Guang Gong, was to build a secure communication system that employs such proxy-assisted protocol as illustrated in figure four.
Introduction
A new protocol called "Controlled Proxy-Assisted Secure End-to-End Communication Protocol" was proposed by Professor Hung-Yu Lin to solve the problem. This protocol removes the computing requirement that imposes on mobile devices by introducing an entity called the Security Proxy. The significance of the Security Proxy is that it has the computing resources to perform asymmetric authentication very fast. Thus the hard computatio steps are shifted from very constrained devices (the mobile stations) to a more powerful trusted server (security proxie). When mobile users want to establish a secure session, the Security Proxy performs the mutual authentication for the mobile devices and enables them to establish a session key. The session key is then used to encrypt all further communications between the mobile station for the period of one sessio nusing symmetric and thus cheap encryption schemes.
Implementation
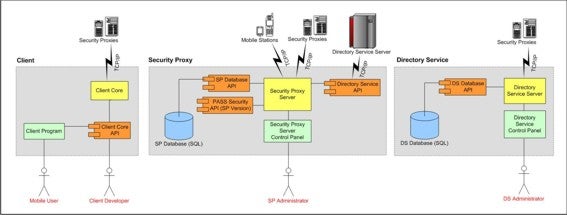
The proxy assisted protocol can be implemented in many different languages using different sofware development kits (SDK). In the fourth year project the students concluded to use .Net framework and Windows Networking SDK to implement the server part and to use Microsoft Structured Query Language (SQL) for the database. The architecture of the components is shown in figure five. The implementation was successfully demonstrated on the forth year design symposium on two mobile clients in two PDAs.
Publication
- H. Lin. "Controlled Proxy-assisted Secure End-to-End Communication", Technical Report, CORR 2002-31, University of Waterloo, 2002. [PS]