Abstract
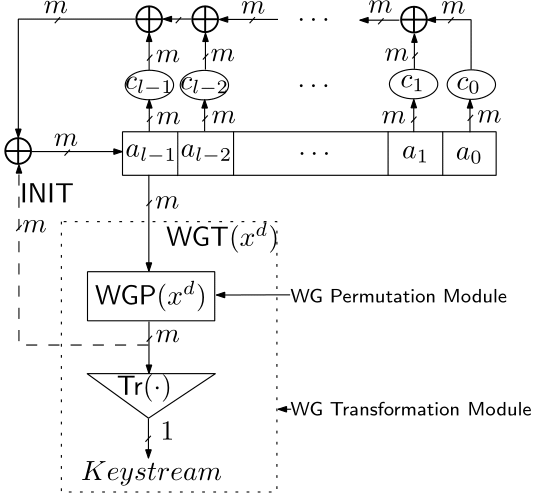
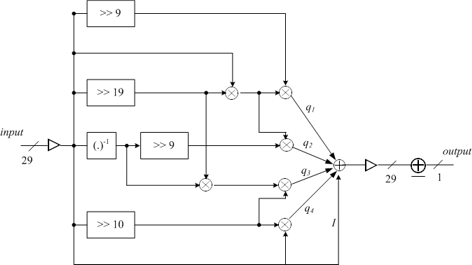
We propose a new synchronous stream cipher, called WG (Welch-Gong) cipher. The cipher is based on WG transformations. The WG cipher has been designed to produce keystream with guaranteed randomness properties, i.e., balance, long period, large and exact linear complexity, three level additive autocorrelation, and ideal two level multiplicative autocorrelation. It is resistant to time/memory/data tradeoff attacks, algebraic attacks and correlation attacks. The cipher can be implemented with a small amount of hardware.
For more information
- Read the full paper: Yassir Nawaz and Guang Gong, "The WG stream cipher", submitted to ECRYPT Stream Cipher Project, The WG Stream Cipher.
- Go to eSTREAM: the ECRYPT Stream Cipher Project. C code is also available at this site.
Publications
- H. El-Razouk, A. Reyhani-Masoleh, and G. Gong, New Hardware Implementations of WG (29, 11) and WG-16 Stream Ciphers Using Polynomial Basis, IEEE Transactions on Computers, IEEE, 2015
- H. El-Razouk, A. Reyhani-Masoleh, and G. Gong, New Implementations of the WG Stream Cipher, IEEE Transactions on Very Large Scale Integration (VLSI) Systems, Vol. 22, No. 9, pp. 1865-1878, IEEE, 2014
- X. Fan, T. Wu, and G. Gong, An Efficient Stream Cipher WG-16 and its Application for Securing 4G-LTE Networks, Applied Mechanics and Materials, Vol. 490, pp. 1436-1450, Trans Tech Publ, 2014
- K. Mandal, G. Gong, X. Fan, and M. Aagaard, Optimal Parameters for the WG Stream Cipher Family, Cryptography and Communications, Vol. 6, No. 2, pp. 117-135, Springer, 2014
- G. Gong, M. Aagaard, and X. Fan, Resilience to Distinguishing Attacks on WG-7 Cipher and their Generalizations, Cryptography and Communications, Vol. 5, No. 4, pp. 277-289, Springer, 2013
- X. Fan, N. Zidaric, M. Aagaard, and G. Gong, Efficient Hardware Implementation of the Stream Cipher WG-16 with Composite Field Arithmetic, Proceedings of the 3rd international workshop on Trustworthy embedded devices, pp. 21-34, ACM, 2013
- G. Yang, and X. Fan, M. Aagaard, and G. Gong, Design Space Exploration of the Lightweight Stream Cipher WG-8 for FPGAs and ASICs, Proceedings of the Workshop on Embedded Systems Security, p. 8, ACM, 2013
- K. Mandal, G. Gong, X. Fan, and M. Aagaard, On Selection of Optimal Parameters for the WG Stream Cipher Family, 2013 13th Canadian Workshop on Information Theory (CWIT), pp. 17-21, IEEE, 2013
- X. Fan, K. Mandal, and G. Gong, WG-8: A Lightweight Stream Cipher for Resource-constrained Smart Devices, Quality, Reliability, Security and Robustness in Heterogeneous Networks, pp. 617-632, Springer, 2013
- M. Aagaard, G. Gong, and R. Mota, Hardware Implementations of the WG-5 Cipher for Passive RFID Tags, 2013 IEEE International Symposium on Hardware-Oriented Security and Trust (HOST), pp. 29-34, IEEE, 2013
- C. Lam, M. Aagaard, and G. Gong, Hardware Implementations of Multi-output Welch-Gong Ciphers, Technical Report, CACR 2011-01, University of Waterloo, 2011
- Y. Luo, Q. Chai, G. Gong, and X. Lai, WG-7, A Lightweight Stream Cipher with Good Cryptographic Properties, IEEE Global Communications Conference -- GLOBECOM, pp. 1-6, 2010
- Y. Nawaz and G. Gong, The WG Stream Cipher, ECRYPT Stream Cipher Project Report 2005, Vol. 33, 2005