Spear phishing attempts, compared to spam and ordinary phishing attacks, are more personalized for the University of Waterloo environment and are called "spear phishing" because of the directed approach they take.
Features of a spear phishing message
The sender is more plausible
- Many phishing attacks appear to come from someone claiming to be from a Nigerian oil company or similar organization offering money. That is likely a business that UWaterloo would not normally work with.
- In a spear phishing attack, the forged email is crafted to be more plausible. It might appear to come from another university, for example.
- Check the sending and return address to see whether the addresses are legitimate. Even if forged, there might be discrepancies in the addresses that will help you identify malicious email.
The email is relevant
- The sender will talk about upgrades to local software, or an unpaid invoice that the University should deal with, rather than asking for help with a money transfer.
The graphics are familiar
- In the email or related web pages, graphics from software used at UW or actual UW logos will be included.
The links in the message may mention UWaterloo in the URL
- Instead of a completely generic URL, the fraudster uses a domain they have control of so words like “uwaterloo” or “uw” are included in the URL.
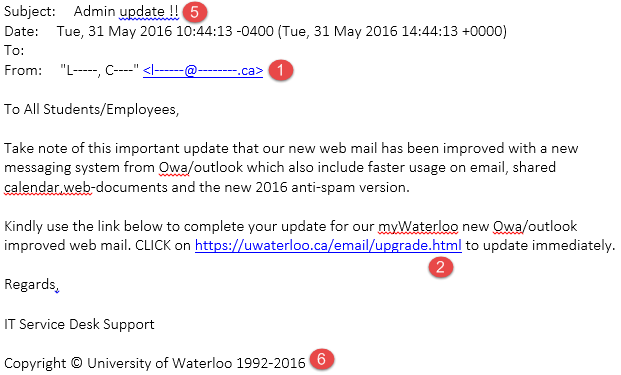
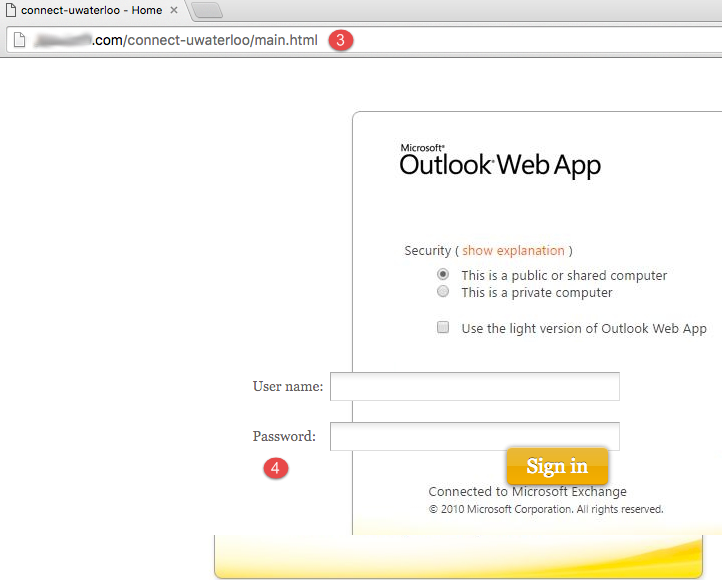
Below is an actual spear phishing email received recently by UWaterloo staff (the identifying portions of the email and website have been removed), crafted to look like it is from the IST Service Desk.
Spear phishing on campus
Spear phishing features
- From email address appears to be from another Canadian university, not Waterloo.
- Email content appear relevant.
- Link text looks legitimate, but the actual link points to a non-Waterloo domain, even though uwaterloo is included.
- Graphics on destination page resemble legitimate graphics, but are slightly wrong.
Other concerns
- Subject does not align with those typically used for legitimate IT service emails.
- Copyright text is never included in legitimate IT service emails.
Protect yourself against spear phishing attacks
- Always check the URL of a link before clicking on it. Don't click if the URL isn't at uwaterloo.ca, or if the URL is unusual or difficult to read.
- If the email claims a software or other upgrade is being done university-wide, verify it by checking with your IT Computing Rep or the IST Service Desk.
- If the email is about something that has nothing to do with your job (like dealing with invoices) ignore it.
- Don't open attachments if the message is from an unknown sender, or if the attachment is irrelevant to your job.
- If the email looks suspicious, verify its legitimacy by phoning or discussing it in person with the sender listed in the email header.
- Report suspicious email messages to IST.