Developed by: Andriana Vanezi, Information Security Services, IST
Preamble by: Ian Milligan, Associate Vice-president, Research Oversight and Analysis
Last updated: May 20, 2025
Preamble
The University of Waterloo, through its Research Data Management (RDM) Institutional Strategy, aims to support research excellence through the provision of excellent RDM services, tools, and supports. In Canada, the Tri-Agencies argue that research data collected using public funds should be responsibly and securely managed and be—where ethical, legal, and commercial obligations allow—available for reuse by others. To this end, the agencies support the FAIR (Findable, Accessible, Interoperable, and Reusable) guiding principles for research data management and stewardship, when appropriate.
Data management, the storage, access, and preservation of data produced from a given research project, is thus a critical component of research activities. Data management practices cover the entire lifecycle of the data, from planning the investigation to conducting it, and from backing up data as it is created and used to long-term preservation of data deliverables after the research investigation has concluded.
In the RDM strategy, the University notes that this strategy was “relevant to all research utilizing and producing research data in all forms (including, but not limited to, digital, analogue, paper, and physical materials)—whether funded or unfunded, published or unpublished, open or restricted.”
Researchers may have questions about whether their data are “open or restricted,” and how they should responsibly steward this information. Canadian research funders, and their institution, want to help researchers share their data (where appropriate) for the advancement of science; we hope this guide helps researchers navigate this landscape.
Purpose
This page provides University of Waterloo (UW) researchers with a standardized framework for classifying research data. By standardizing the classification of research data, a mutual understanding of the associated risk levels is established. This shared framework facilitates effective communication and collaboration among impacted/interested parties, with an institutionally accepted classification. Researchers can identify and engage expertise who can provide meaningful and appropriate support tailored to the specific needs associated with the data risk classification. This collaborative and standardized approach enhances the overall data governance structure, promoting a cohesive effort in safeguarding research data and maintaining compliance with regulatory standards and contractual obligations to research sponsors, when applicable.
While the University of Waterloo’s Policy 46 Information Confidentiality Classification is aligned with the Freedom of Information and Protection of Privacy Act (FIPPA), to protect data used for teaching, learning, and research administration, it was not designed to classify research data. However, the research data risk classification will align with the confidentiality classification outlined in Policy 46, allowing the proposed security controls to be effectively applied across both classifications. See Guidance on Information Confidentiality Classification (Policy 46) | Information Systems & Technology | University of Waterloo. For more details on what constitutes research data, including its definition and examples, see Research Data and Information Not Considered Research Data.
Information Systems & Technology/Information Security Services (ISS/IST) in consultation with Research Data Management Institutional Strategy Working Group, has developed a six (6) step framework to provide researchers with a structured approach to classifying their research data by assessing the potential harm that could arise from compromises. Please see the full document:
Research data risk classification
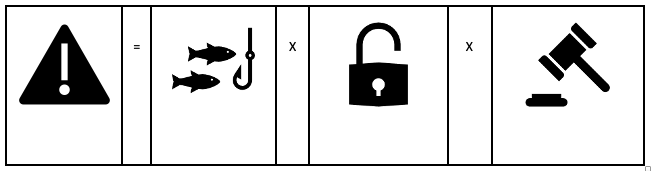
The Research Data Classification System is based on two main factors: the type of data and the potential gravity of harm that could arise from a compromise.
In cases of ambiguity in research data classification, the higher risk category should be applied. If uncertainty persists, please contact Information Security Services for guidance. For assistance with classifying human participant data, please contact the Office of Research Ethics.
Low
Research data are open or publicly available, a compromise to the integrity or availability of data would cause minimal harm to impacted/interested parties.
Examples (not exhaustive):
|
TYPE OF DATA |
POTENTIAL HARM - MILD |
|---|---|
|
|
Medium
Research data are typically confidential, even if they are not specifically potentially governed by domestic or foreign laws or industry regulations; any compromise to the confidentiality, integrity or availability could lead to mild-to-moderate harm to impacted/interested parties.
Examples (not exhaustive):
|
TYPE OF DATA |
POTENTIAL HARM - MILD TO MODERATE |
|---|---|
|
|
High
Research data are confidential and/or potentially governed by domestic or foreign laws or industry regulations; a compromise to the confidentiality, integrity or availability of data would cause significant harm to impacted/interested parties.
Examples (not exhaustive):
|
TYPE OF DATA |
POTENTIAL HARM – SIGNIFICANT |
|---|---|
|
|
Very High
Research data are confidential, and/or potentially governed by domestic or foreign laws or industry regulations, or Indigenous data sovereignty, and any compromise to the confidentiality, integrity or availability of data could cause serious harm to impacted/interested parties.
Examples (not exhaustive):
|
TYPE OF DATA |
POTENTIAL HARM - SERIOUS |
|---|---|
|
|
Roles and responsibilities
Policy 46 – Information Management outlines distinct roles and responsibilities for research team members. Under this policy, the Principal Investigator or Faculty Supervisor for research projects is the information steward for the research data while other research team members for the research project are information custodians. There may be times when this approach is different, for example, in the context of when researchers are engaging with Indigenous communities.
Engage expertise
Identify individuals or teams within the University of Waterloo who can provide guidance on various aspects of the research project regarding data management (e.g., IT specialists, legal advisors, data management experts).