IQC researchers have developed a method to simplify the analysis of quantum communication protocols compatible with existing telecommunications infrastructure.
One of the exciting technologies enabled by quantum mechanics is quantum key distribution (QKD), which allows two parties to establish a shared, secret key protected by the laws of nature. The two parties can detect if an eavesdropper attempts to interfere with their communication, which is not possible using classical systems. If significant eavesdropping activity is detected, the parties can simply abandon the protocol and try again.
“The exciting thing about quantum key distribution is that it is already being implemented experimentally,” said Twesh Upadhyaya, a Master’s student at IQC and the Department of Physics and Astronomy, and lead author on the paper. “With the right protocols, QKD can even be implemented on a large scale using existing telecommunications infrastructure.”
The problem? These protocols are much more challenging to analyze.

Twesh Upadhyaya
Information is encoded into pulses of laser light sent from Alice to Bob. After an eavesdropper Eve interacts with the pulses, each pulse can have anywhere from 0 to an infinite number of photons, making the quantum state infinite-dimensional. That is, you would need an infinite number of rows and columns to write down the state as a matrix. This becomes a challenge when researchers are trying to study the security of these protocols quantitatively. It's not possible to numerically optimize over these infinite-dimensional states, because computers only have a finite memory.
Upadhyaya, along with coauthors PhD student Jie Lin, postdoc Thomas van Himbeeck, and Prof. Norbert Lütkenhaus, developed a dimension reduction method to solve this problem, which relates this infinite-dimensional scenario to a simpler finite one, making security analysis possible with existing numerical tools.
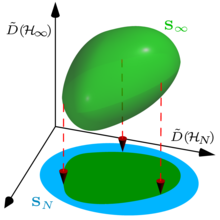
“We found a security proof that doesn’t rely on previous assumptions, but still gives as good a performance,” said Upadhyaya. “We also found that our method is like a faster, more generalizable version of another type of proof method which only applies to a restricted class of protocols.”
The researchers’ dimension reduction method is general, so Upadhyaya expects it will assist in analyzing other QKD protocols that might be useful for the quantum communication networks of the future. He also thinks they can extend the framework to explore other interesting questions in QKD, entanglement verification and quantum information more generally.
“One huge benefit of numerical tools is their flexibility. Things in the real world are never as clean as in homework problems. Devices are noisy, environments have disturbance and so on, but these things can be modelled. So, it’s nice that our method reduces infinite-dimensional problems to something our existing numerical tools can handle.” The implementation of the tools builds on the group’s numerical framework for key rate calculations, which is slated for an upcoming open source release.
A future where large-scale quantum communication networks secure our most important information is one step closer, with analytical capabilities catching up to experimental capabilities.
Dimension Reduction in Quantum Key Distribution for Continuous- and Discrete-Variable Protocols was published in PRX Quantum on May 24, 2021.