Each year, the Cheriton Research Symposium concludes with a poster session for Cheriton Graduate Scholarship recipients. In total, 23 students participated in the 2018 Cheriton Research Symposium poster competition.

Posters were on display in the Great Hall in the Davis Centre, as graduate students explained the theory behind and the results and impacts of their research to David R. Cheriton and a panel of judges from the School of Computer Science.
We are delighted to announce the winners of the 2018 Cheriton Research Symposium poster competition.
First-place winners (tie) — $300 prize
Amine Mhedhbi and Siddhartha Sahu for “The Ubiquity of Large Graphs and Surprising Challenges of Graph Processing” (This research also received the VLDB 2018 Best Paper Award.)

Sidhartha Sahu (centre), Amine Mhedhbi (right)
Sajin Sasy for “ZeroTrace: Oblivious Memory Primitives from Intel SGX”

Second-place winners (tie) — $200 prize
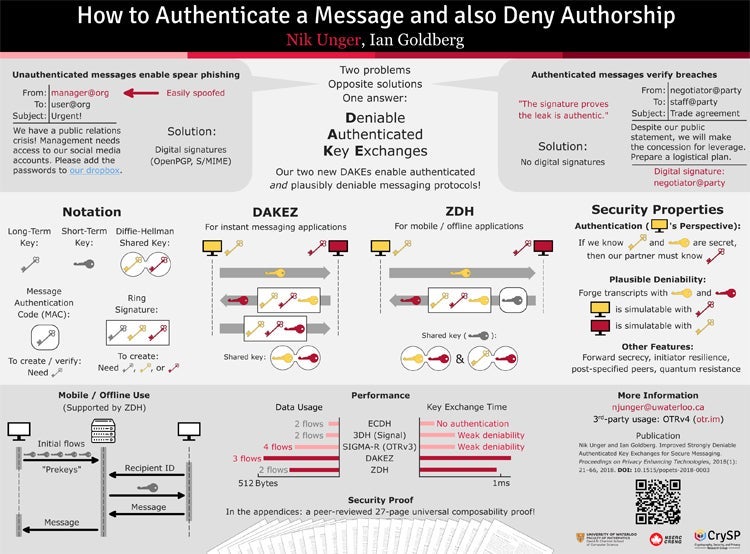
Nik Unger for “How to Authenticate a Message and also Deny Authorship” (This research was also the runner-up for the 2018 Caspar Bowden Award for Outstanding Research in Privacy Enhancing Technologies.)
Linguan Yang for “Carousel: Low-Latency Transaction Processing for Globally-Distributed Data”

Third-place winners (tie) — $100
Thomas Lidbetter for “Additive Number Theory via Approximation by Regular Languages”

Xin Lian for “Fault-tolerant Multi-Label Hierarchical Classification with OT distance”

Congratulations to the winners and thanks to all who participated in the contest!
Poster competition judges
Thanks to Professors Lila Kari (Chair), Eric Schost, Samer Al-Kiswany, Omid Abari and Ali Mashtizadeh, who gave generously of their time to judge the posters and student presentations.
Poster competition participants
| Poster presenter | Supervisor | Title |
|---|---|---|
|
Rylo Ashmore | Richard Trefler, Arie Gurfinkel | Local Verification of Distributed Systems |
| Joseph Haraldson | Mark Giesbrecht, George Labahn | Computing Nearby Non-Trivial Smith Forms |
| Jeremy Hartmann | Daniel Vogel | An Evaluation of Mobile Phone Pointing in Spatial Augmented Reality |
| Joshua Jung | Jesse Hoey | Automating the Intentional Encoding of Human-Designable Markers |
| Mikhail Kazhamiaka | Bernard Wong, Khuzaima Daudjee | Towards a Disaggregated Consensus Protocol |
| Xiaowei Kuang | Edith Law, Kate Larson | Evaluation of an Interpretable EEG Sleep Staging Model with Non-expert Users |
| Amit Levi | Eric Blais | Tolerant Junta Testing and the Connection to Submodular Optimization and Function Isomorphism |
| Xin Lian | Yaoliang Yu | Fault-tolerant Multi-Label Hierarchical Classification with OT Distance |
|
Thomas Lidbetter | Jeffrey Shallit | Additive Number Theory via Approximation by Regular Languages |
| Amine Mhedhbi | Semih Salihoglu | The Ubiquity of Large Graphs and Surprising Challenges of Graph Processing (with Siddhartha Sahu) |
| Alex Norton | Florian Kerschbaum | Compiling ZK Proofs for Maliciously Secure Multiparty Computation |
| Anil Pacaci | M. Tamer Özsu | Distribution-Aware Stream Partitioning for Distributed Stream Processing Systems |
| Marianna Rapoport | Ondřej Lhoták | DOT DOT DOT: Three Additions to Dependent Object Types |
| Siddhartha Sahu | Semih Salihoglu | The Ubiquity of Large Graphs and Surprising Challenges of Graph Processing (with Amine Mhedhbi) |
| Reza Adhitya Saputra | Craig Kaplan | RepulsionPak: Deformation-Driven Element Packing |
| Sajin Sasy | Ian Goldberg, Sergey Gorbunov | ZeroTrace: Oblivious Memory Primitives from Intel SGX |
| Nashid Shahriar | Raouf Boutaba | Achieving a Fully-Flexible Virtual Network Embedding in Elastic Optical Networks |
| Hemant Surale |
Daniel Vogel |
Experimental Analysis of Barehand Mid-air Mode-Switching Techniques in Virtual Reality |
| Meng Tang |
Yuri Boykov | Regularized Losses for Weakly-supervised CNN Segmentation |
| Sverrir Thorgeirsson |
Chris Eliasmith |
Action Selection in Spiking Neural Models |
| Nik Unger | Ian Goldberg | How to Authenticate a Message and also Deny Authorship |
| Zihao Wang |
Lila Kari | Word Blending |
| Linguan Yang | Bernard Wong |
Carousel: Low-Latency Transaction Processing for Globally-Distributed Data |