Computer scientists at the Cheriton School of Computer Science have developed a new system that helps Internet users ensure their online data is secure. Called Mitigator, the software-based system includes a plugin that users can install in their browser, which will give them a secure signal when they visit a website verified to process its data in compliance with the site’s privacy policy.
“Privacy policies are really hard to read and understand, and now with COVID-19 so many people are doing so much more online that privacy policies are more important than ever,” said Miti Mazmudar, a PhD candidate in the Cryptography, Security, and Privacy (CrySP) research group.
Although research has been conducted into alternative representations of privacy policies, the systems that have been developed do not determine whether website providers adhere to the data handling practices outlined in their privacy policies.
“What we try to do is have a compliance system that takes a simplified model of the privacy policy and checks the code on the website’s end to see if it does what the privacy policy claims to do,” Miti Mazmudar continued. “If a website requires you to enter your email address, Mitigator will notify you if the privacy policy stated that this wouldn’t be needed or if the privacy policy did not mention the requirement at all.”
Mitigator can work on any computer, but the companies that own the website servers must have machines with a trusted execution environment — a secure area of modern server-class processors that guarantees the protection of code and data loaded in it with respect to confidentiality and integrity. The Mitigator implementation is prototyped using the Intel Software Guard Extensions (SGX) trusted hardware platform.
Mitigator’s main contribution is in designing an architecture that uses an underlying trusted hardware platform to run a program — called the decryptor — that hands users’ data only to a target program that has been determined to be compliant with a privacy policy model. As both of these programs are run on a trusted hardware platform, users can verify that the decryptor is indeed the correct, unmodified program.
“The big difference between Mitigator and prior systems that had similar goals is that Mitigator’s primary focus is on the signal it gives to the user,” said Ian Goldberg, a Professor at the Cheriton School of Computer Science and the Canada Research Chair in Privacy Enhancing Technologies.
“The important thing is not just that the company knows their software is running correctly; we want the user to get this assurance that the company’s software is running correctly and is processing their data properly and not just leaving it lying around on disk to be stolen. Users of Mitigator will know whether their data is being properly protected, managed, and processed while the companies will benefit in that their customers are happier and more confident that nothing untoward is being done with their data.”
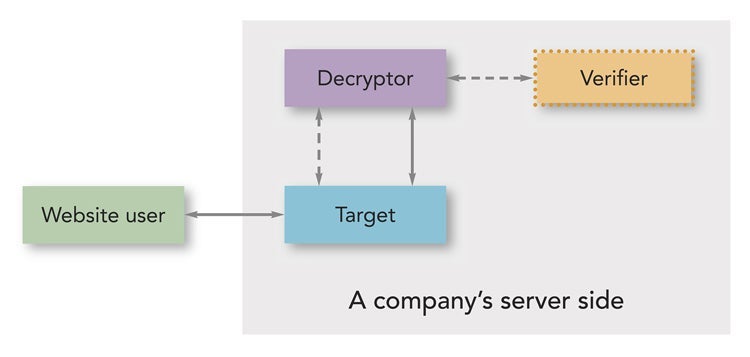
Block
diagram
of
the
Mitigator
system.
Mitigator
has
three
stages.
The
first
stage
runs
as
a
website’s
source
code
is
being
developed.
During
this
stage
the
verifier
enclave
checks
the
source
code
and
privacy
policy
for
compliance.
If
the
code
complies
with
the
privacy
policy,
it
outputs
a
signed
target
enclave.
If
the
code
does
not
comply
with
the
privacy
policy,
developers
are
expected
to
modify
their
source
code
and
privacy
policy
and
rerun
the
system
until
it
passes
as
compliant.
The
second
stage
occurs
once
the
target
enclave
is
ready
to
be
deployed.
Here,
the
decryptor
enclave
conducts
local
attestation
with
both
enclaves.
The
third
stage
refers
to
runtime
interactions
between
the
website
user,
target,
and
decryptor
enclaves.
In
this
stage,
the
website
user
passes
encrypted
form
field
data
to
the
target
enclave,
which
in
turn
securely
hands
it
over
to
the
decryptor
enclave.
A paper detailing this study, titled “Mitigator: Privacy policy compliance using trusted hardware,” was written by Miti Mazmudar and Ian Goldberg. Their paper was accepted for presentation at PETS 2020, the 20th Privacy Enhancing Technologies Symposium, which will be held virtually from July 14 to 18, 2020. The paper will be published in the open-access journal Proceedings on Privacy Enhancing Technologies (PoPETs).